
Windows 10 operating system users are once again facing a looming threat of virus infection. A rapidly spreading hijacking malware, codenamed Adrozek is currently targeting all browsers, including Google Chrome, Mozilla Firefox, and Microsoft Edge.
Microsoft has issued an emergency warning about malware that hijacks search results with ads. While this may not seem harmful, some variants of the malware even steal user passwords and other login credentials.
Adrozek hijacking malware modifies browser settings to conduct attacks:
The Adrozek malware is targeting Google Chrome, Mozilla Firefox, Microsoft Edge, and Yandex browsers. Attackers have designed the malware campaign to inject ads into search results and install malicious browser extensions.
The newly discovered malware family has been operational since at least May this year. The attacks peaked in August. Security software manufacturers and cybersecurity teams identified the threat and indicated that the malware might be spreading at a rate of more than 30,000 devices every day.
Adrozek Malware Delivers Fake Ads to 30K Devices a Day https://t.co/oubp6oGaLN https://t.co/x7518Tw83m #infosec
— Nicolas Dewaele (@nicodewaele_fr) December 11, 2020
The strains belonging to the Adrozek malware campaign attempt to lead users to affiliated pages. The malware serves malware-inserted ads on search results. However, as part of its initiation sequence, the malware silently adds malicious browser extensions.
It also manipulates and changes browser settings to insert ads into webpages. These malicious ads often appear on top of legitimate ads from search engines.
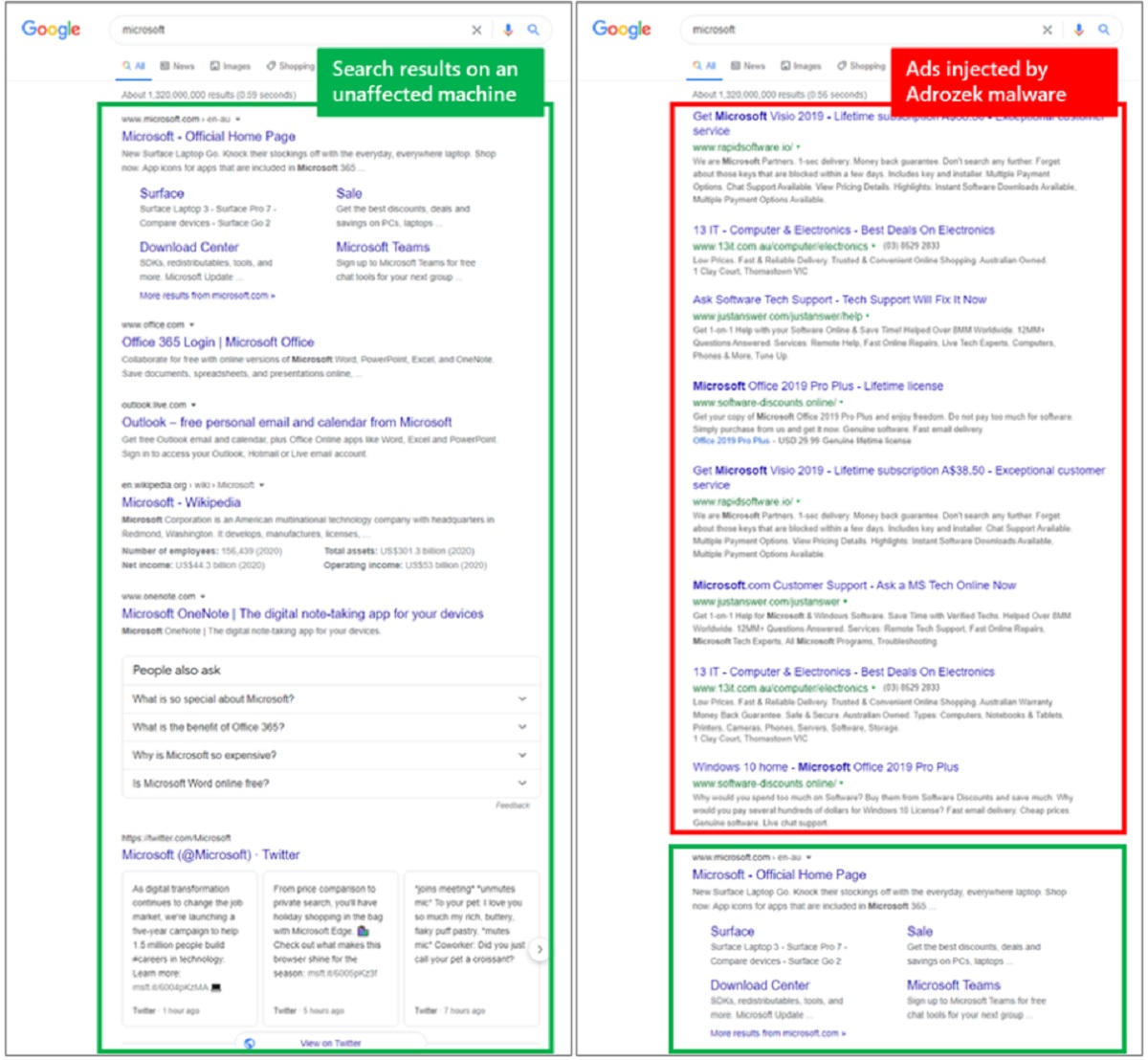
Some experts indicated the malware can also modify DLL per target browser, MsEdge.dll on Microsoft Edge, for instance, to turn off security controls. Simply put, the Adrozek malware campaign is smart enough to switch off warnings, initiate the installation of malicious browser extensions, and inject its own ads that appear legitimate to a user.
Why is Adrozek hijacking malware a dangerous and concerning threat to Microsoft Windows 10 users?
What makes Adrozek different from other malware threats is that it installs itself on devices “though drive-by download” methodology. In other words, the installer file for the malware carries a standard format of setup_.exe.
When run or executed, the installer drops an executable or .exe file with a random file name in the temporary folder, which, in turn, drops the main payload in the Program Files folder. Concerningly, the malware ensures the payload looks like a legitimate audio-related software and carries names like Audiolava.exe, QuickAudio.exe, or converter.exe.
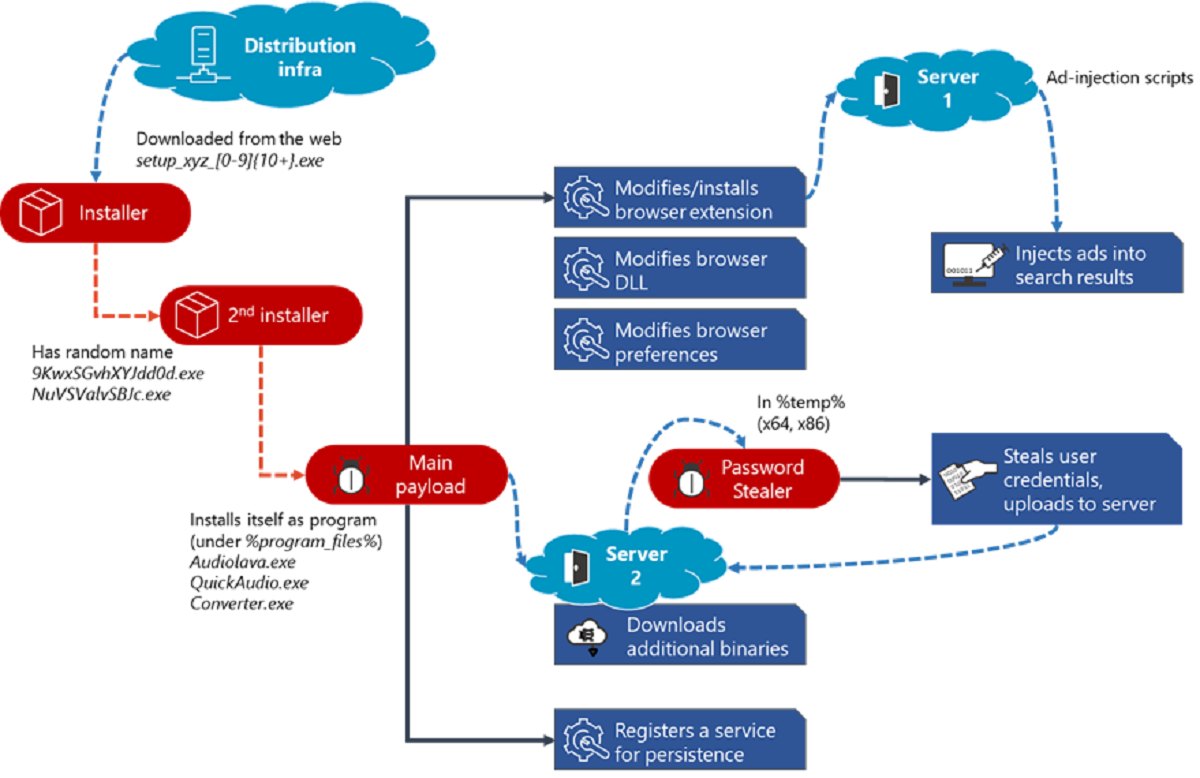
It is even more concerning to note this ‘hiding in plain sight’ approach of the Adrozek hijacking malware. Security researchers noticed the malware installs just like a usual program. Windows 10 users can even access the malicious program through the Apps & features settings of the OS.
The Adrozek hijacking malware registers itself as a Windows service with the same name. Needless to add, such overt tricks have been successful in preventing the malware from getting caught by ordinary antivirus software through routine checks.
How to protect Windows 10 OS and web browsers from Adrozek hijacking malware?
There is no doubt the Adrozek hijacking malware is dangerous. The creators of the malware have ensured their creation can establish a secure connection to unknown servers and send information as well as download more malicious code.
Moreover, Adrozek malware can prevent browsers from updating themselves. The malware simply switches off the ‘Auto Update’ feature.
Adrozek Malware Delivers Fake Ads to 30K Devices a Day https://t.co/oubp6oGaLN https://t.co/x7518Tw83m #infosec
— Nicolas Dewaele (@nicodewaele_fr) December 11, 2020
The only solution to protect from Adrozek hijacking malware is to install a reliable ‘Endpoint’ antivirus or security solution. Microsoft obviously recommends Microsoft Defender Antivirus, which is a free built-in security suite within Windows 10.
Microsoft Defender Antivirus and quite a few reputed security suites have endpoint protection solutions. These use behavior-based, machine learning-powered detection to block malware families including Adrozek.


